1. High-level authentication flow
The authetication flow
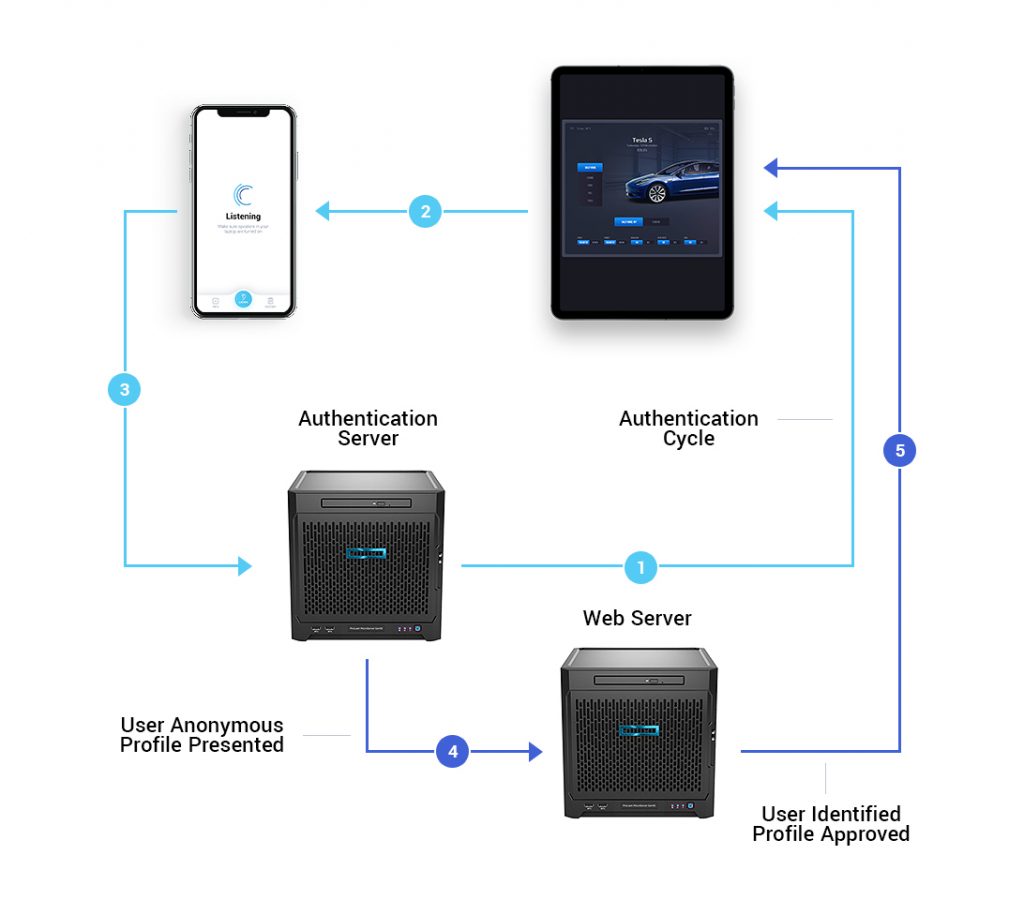
- A randomly generated one-time token is pushed from the Cyberus Key Authentication server to a device, which emits the one-time ultrasonic message.
- The nearby recipient device picks up the ultrasonic communication and uses a patented algorithm to extract the one-time token.
- The one-time token is sent back to the Authentication server, along with identifying information about the receiving device, further validating the security of the communication.
- The Authentication server confirms both sides of the transaction are authentic, protecting your company as well as your customers. The server then sends confirmation that the transaction can proceed.
- With the devices authenticated and linked, a secure communication channel is opened allowing the exchange of identity, payment or any other information.
At its core, the login process is based on a one-time transaction token which means no ‘actionable’ login credentials (user IDs or passwords) are used/stored anywhere or during the authentication cycle and thereby there are no credentials of any value for hackers to steal.